Introduction
This Age Verification Solution is composed of several modular components that serve as a blueprint for developing a national or organizational implementation. Additional features and enhancements are currently under development. Please refer to the Roadmap section for more details.
To make your first steps as simple as possible, you can use pre-configured services hosted by the project. These services are intended solely for testing and demonstration purposes, not for production use. They allow you to quickly experience and evaluate the application without extensive setup or configuration.
In this Getting Started guide, we explain the hosted services provided by the project and how you can make use of them. If you prefer to run the services locally, please see the Setup section for further instructions.
Core Components
The Age Verification Solution consists of four main components designed to provide a secure and seamless onboarding and verification experience:
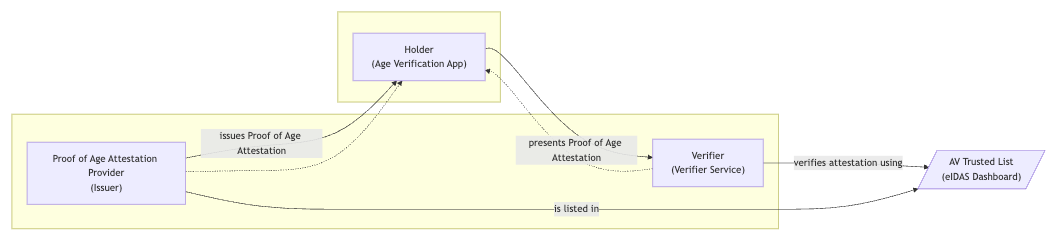
1. Mock Issuer Service
This service issues Proof of Age Attestations and is primarily used during onboarding. When a user configures the Age Verification App, the mock issuer can provide a batch of attestations, allowing for straightforward testing and integration without requiring real identity sources.
2. Age Verification App
The Age Verification App securely stores the received Proof of Age Attestations on the user’s device. It is designed with privacy and security in mind, ensuring that sensitive information is protected at all times.
3. Verifier Service
The Verifier represents a typical service provider who accepts and validates Proof of Age Attestations. For demonstration purposes, we have included a visualization feature within the test verifier service, making the validation process transparent and easier to understand.
4. eIDAS Dashboard & Trusted List
An Age Verification Trusted List is made available via the eIDAS dashboard. This trusted list contains the public key of the issuer and is referenced by the verifier to ensure that only attestations issued by a legitimate and recognized issuer are accepted. This mechanism provides an additional layer of trust and aligns with the requirements of the eIDAS framework.
In summary, these components enable a full demonstration workflow, from issuance and storage to verification, while ensuring that trust and security requirements are met at every step.
On-boarding Flow
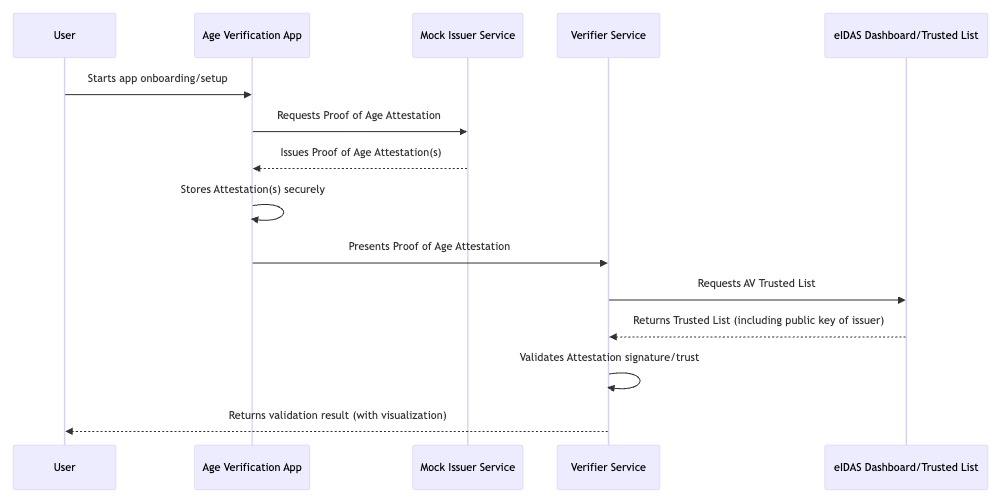
The following sequence diagram illustrates the main interactions between the core components of the Age Verification Solution during the user onboarding and age verification process:
-
The user initiates the onboarding process by starting the Age Verification App.
-
The app requests a Proof of Age Attestation from the Mock Issuer Service.
-
The Mock Issuer Service issues one or more Proof of Age Attestations and returns them to the app.
-
The app securely stores the received attestations.
-
When required, the app presents a Proof of Age Attestation to the Verifier Service.
-
The Verifier Service requests the Age Verification Trusted List from the eIDAS Dashboard to validate the public key of the issuer.
-
The eIDAS Dashboard returns the Trusted List, including the issuer’s public key.
-
The Verifier Service validates the attestation by checking its authenticity, integrity, trust status and claim value.
-
Finally, the Verifier Service returns the validation result directly to the user.
This diagram highlights the trust chain and the flow of data between the user, app, issuer, verifier and the trusted list, ensuring secure and privacy-compliant age verification.